It can be challenging to keep up with the ever-evolving cyber threat landscape. Companies need to process large amounts of data. As well as respond to incidents quickly and effectively. Managing an organization's security posture is complex.
That's where Microsoft Security Copilot comes in. Microsoft Security Copilot is a generative AI-powered security solution. It provides tailored insights that empower your team to defend your network. It works with other Microsoft security products. It also integrates with natural language to generate tailored guidance and insights.
In this article, we will explain what Microsoft Security Copilot is. We’ll explore its benefits and whether it's the right choice to enhance your digital defenses.
What Is Microsoft Security Copilot?
Microsoft Security Copilot is a cutting-edge cybersecurity tool. It leverages the power of AI and machine learning for threat detection and response. Copilot aims to enhance the efficiency and effectiveness of cybersecurity operations.
Microsoft Security Copilot helps security teams:
- Respond to cyber threats
- Process signals
- Assess risk exposure at machine speed
It works with other Microsoft security products as well. A big benefit is that it integrates with natural language. This means you can ask questions plainly to generate tailored guidance and insights.
Security Copilot can help with end-to-end scenarios such as:
- Incident response
- Threat hunting
- Intelligence gathering
- Posture management
- Executive summaries on security investigations
How Does Microsoft Security Copilot Work?
You can access Microsoft Security Copilot capabilities through a standalone experience. As well as embedded experiences available in other Microsoft security products.
Copilot integrates with several tools, including:
- Microsoft Sentinel
- Microsoft Defender XDR
- Microsoft Intune
- Microsoft Defender Threat Intelligence
- Microsoft Entra
- Microsoft Purview
- Microsoft Defender External Attack Surface Management
- Microsoft Defender for Cloud
You can use natural language prompts with Security Copilot. This makes it easy to ask for information or guidance on various security topics.
For example, you can ask:
- What are the best practices for securing Azure workloads?
- What is the impact of CVE-2024-23905 on my organization?
- Generate a report on the latest attack campaign.
- How do I remediate an incident involving TrickBot malware?
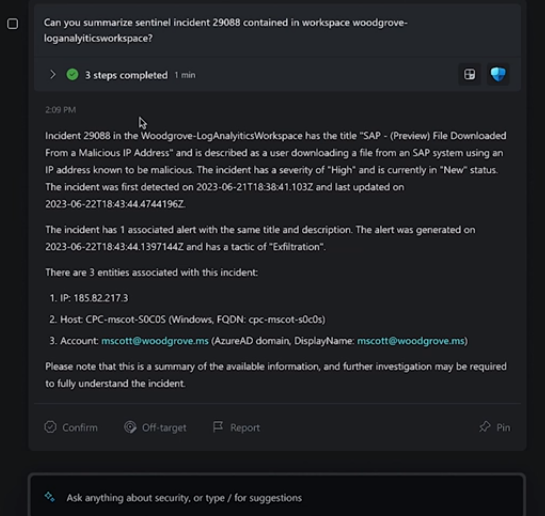
Should You Use Microsoft Security Copilot?
The Pros:
- Advanced Threat Detection
Microsoft Security Copilot employs advanced algorithms. These detect and analyze threats that may go unnoticed by traditional security measures. It has the ability to adapt to new threats in real time. This enhances the security posture for organizations.
- Operational Efficiency
Copilot automates threat analysis. This allows security teams to focus on strategic decision-making. It also reduces the time and effort spent on manual data analysis. The tool streamlines workflows, enabling quicker responses to potential threats.
- Integration with Microsoft Products
Microsoft Security Copilot seamlessly integrates with several Microsoft products. This creates a comprehensive cybersecurity ecosystem. The synergy between these tools enhances threat visibility as well as response capabilities.
- Continuous Learning
The AI and machine learning components of Copilot continuously learn from new data. This improves their ability to identify and mitigate emerging threats over time. This adaptive learning approach ensures that the tool evolves. Which is important to do alongside the ever-changing threat landscape.
- Reduced False Positives
Copilot's advanced algorithms contribute to a more accurate threat detection process. This minimizes false positives that can overwhelm security teams. The result is a more focused and efficient response to genuine threats.
The Considerations:
- Integration Challenges
Microsoft Security Copilot seamlessly integrates with Microsoft and other security products. But organizations using a diverse range of cybersecurity tools may face integration challenges. Consider the compatibility of Copilot with your existing cybersecurity infrastructure.
- Resource Requirements
The deployment of advanced AI and machine learning technologies may demand extra resources. Companies should check if their existing infrastructure supports the requirements of the tool.
- Training and Familiarization
Successfully leveraging the benefits of Copilot requires training. As well as familiarization with the tool's functionalities. Ensure that your security team is adequately trained. This will maximize the potential of this cybersecurity solution.
The Bottom Line
Microsoft Security Copilot represents a leap forward in the realm of AI-driven cybersecurity. It has an advanced capacity for real-time threat detection and operational efficiency. As well as extensive integration capabilities. These factors make it a compelling choice. Especially for businesses seeking to fortify their
digital defenses.
Your unique business needs should guide the decision to adopt Microsoft Security Copilot. Consider factors such as existing cybersecurity infrastructure and resource availability. As well as the commitment to ongoing training.
Get Expert Microsoft Product Support Here!
Microsoft is a vast ecosystem of interconnected business tools. Security Copilot is one of the newest to help you secure your online landscape. If you need some help leveraging these tools for your company, let us know. We are experienced Microsoft service providers. Our team can help you make the most of these tools.
Contact us today to schedule a consultation.
This Article has been Republished with Permission from The Technology Press.



